Many enterprises are shifting to cloud computing for business expansion, saving on cost, growth, and staying ahead of competitors. But, to do so, they are also exposing their business to new risks and challenges. Hence, to protect the companies’ data from known and unknown threats, they need to secure their cloud environment with the right tools.
One can find many tools available online that can help organizations secure their cloud environments, including CASB, CWPP, and CSPM. According to the International Data Services (IDC) report, public cloud spending is estimated to reach $500 billion by 2023.
Adoption of public cloud services will continue in the coming years in various global sectors, including retail, telecommunications, etc. Many enterprises also use Office 365 or Salesforce services to store or transfer data in the cloud.
In a way, more and more data are being exposed in the clouds. According to Statista, in the 2021 survey, 64% of respondents said data loss or leakage is one of the biggest challenges they faced with cloud computing. Similarly, data privacy ranked as the second most challenging.
Users cannot view or handle their data correctly in the cloud, which leads to compromised credentials, data theft, authentication breaches, account hijacking, etc.
Hence, to improve your cloud data security, we have come up with the top cloud security solution that adds an additional protection layer for employees accessing cloud services.
Here, we will compare three CASB, CWPP, and CSPM cloud security technologies, making it easier for organizations to choose the right tool to secure cloud environments.
What is Cloud Access Security Broker (CASB)?
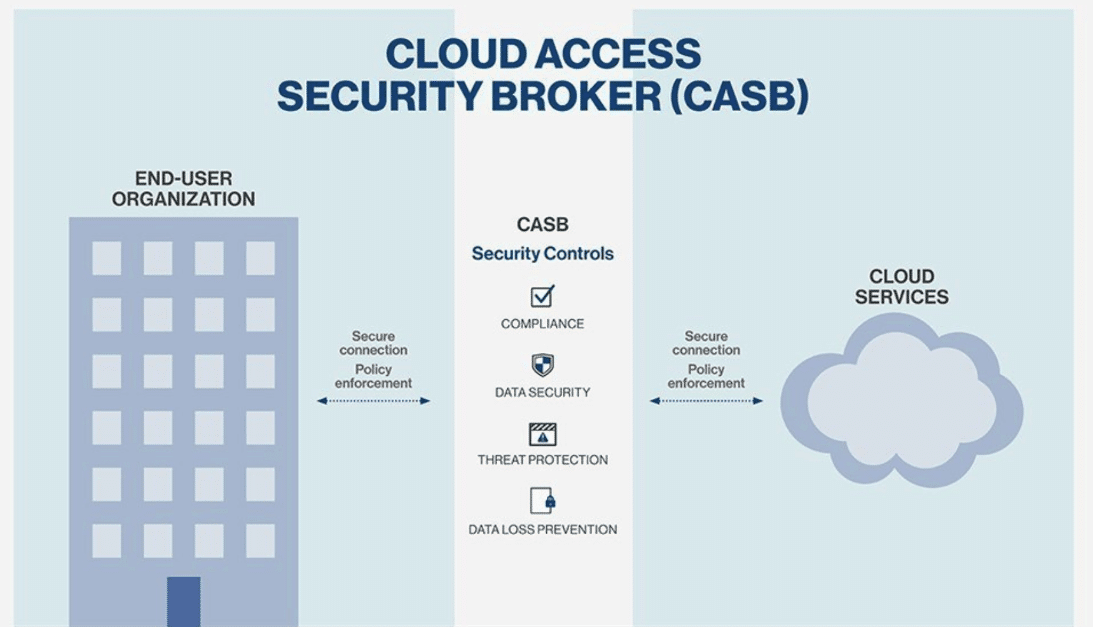
The Cloud Access security broker (CASB) is a gateway that allows only authorized users to access data and detects high-risk applications in real-time. It is a firewall for cloud services that monitors all managed and unmanaged SaaS and PaaS products (shadow IT) and updates the employees on detecting any suspicious event.
CASB solutions are highly beneficial for organizations and support several security access controls that help track, monitor, and report shadow IT issues faster. With CASB, it doesn’t matter where you access the managed and unmanaged device. It enables businesses to keep track of all activities and provides advanced threat protection.
Another feature that makes the security tool a good choice for your business is it offers auditing and reporting tools that support message filtering, user authentication, URL filtering, malware detection, sandboxing, anti-phishing protection, and more.
Enterprises can detect threats and prevent data on time with the help of the CASB solution. Additionally, it offers granular access controls to enforce data-centric security policies.
It is one of the best tools an organization can adopt to extend its security reach beyond its infrastructure.
Visibility, Compliance, Data Security, and Threat Protection are the main pillars of the CASB solution.
Once installed, a CASB solution helps verify user credentials, identifies and blocks malware, and prevents unauthorized transmission of sensitive data from one location to another. Businesses can deploy the solution as API-based or proxy-based and detect threats in real-time.
Further, to maximize protection, organizations can also integrate the CASB solution with existing SIEM enterprise security.
What Does CASB Offer To Secure Your Enterprise Data in Cloud
CASB offers the following features that helps organizations to secure their data in Cloud:
- IAM and SSO integration
- Threat detection and protection
- User and Entity Behavior Analytics
- Malware detection
- Data loss prevention
- Cloud governance with risk assessment
- Data encryption and decryption
- Auditing configurations
What is Cloud Workload Protection Platform (CWPP)?
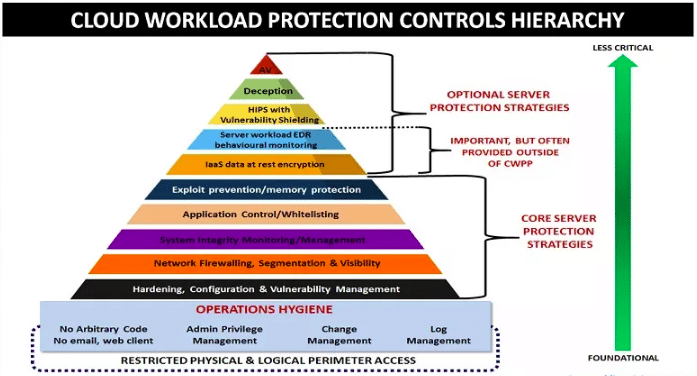
Cloud Workload Protection Platform is a highly distributed security tool that protects all workloads by offering clear visibility across on-premises and cloud environments. Most companies use CWPP solutions to protect their applications, containers, network resources, physical servers, virtual machines (VMs), and serverless workloads.
These solutions protect your workloads from being compromised and secure devices from large attacks. It further allows employees to identify, monitor, and track all misconfigurations and vulnerabilities in real-time, which helps reduce the chances of online threats.
Cloud Workload Protection Platforms can easily integrate security into DevOps CI/CD pipelines and help businesses save on cost with its usage-based billing features.
It is a flexible and cost-efficient cloud security tool that makes it easier for developers to monitor and manage multi-cloud deployments using its single console. Another advantage of choosing Cloud Workload Protection Platforms is they automate the vulnerability scanning process and compliance violations.
If you want to add a protection layer to your cloud workloads, then investing in Cloud Workload Protection Platforms is the right thing to do. With Cloud workload security solutions, businesses can timely detect, secure, and manage their workloads.
What Does CWPP Offer To Secure Your Enterprise Data in Cloud
CWPP offers the following features that help to secure your data in Cloud:
- Application control and allowlisting.
- Anti-malware scanning and system integrity management
- Log management and monitoring
- Workload configuration, visibility, and microsegmentation.
- Broader view of your security workload
- Network segmentation, traffic visibility, firewalling and vulnerability management.
- Offers “Host-based Intrusion Detection System” for improved workload behavior monitoring
- Container and serverless protection
Cloud Security Posture Management (CSPM)
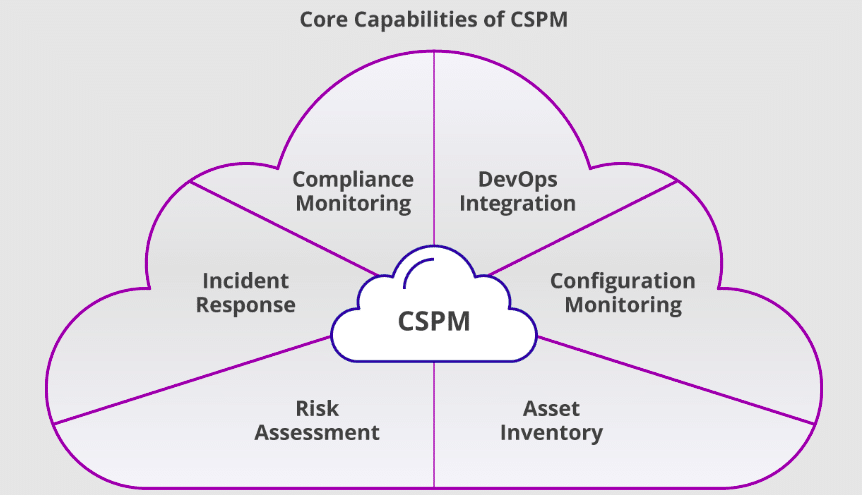
CSPM is a group of security products and services that helps your organization to be proactive, assess risk, reduce misconfigurations, and more. Further, it enables employees to find ways to ensure that your cloud ecosystem uses the highest cloud security measures to protect critical business data.
CSPM also provides continuous compliance monitoring, configuration anomaly prevention, and Trust Center investigation by identifying unknown or high risks in an organization’s cloud fabric, including cloud services for computing, storage, identity, and access.
Users can implement continuous and automated security and compliance processes, primarily to protect the infrastructure where workloads are deployed with the help of the Cloud Security Post Management (CSPM) solution.
The tool is suitable for monitoring the cloud environment and enables businesses to create a policy that helps define the actual state of cloud infrastructure. Further, with the help of CSPM tools, companies can reduce permission errors and misconfigurations and prevent data storage exposed to the public.
Most organizations use the CSPM strategy for DevOps integrations, visualizing and assessing associated risks, and extending the security of cloud environments. There are many benefits Of Cloud Security Posture Management (CSPM) which is why companies trust it more, including real-time visibility, automated security, discovering compliance risks in the cloud, and enabling businesses to monitor existing resources.
What Does CSPM Offer To Secure Your Enterprise Data in Cloud
CSPM protects the cloud environment by identifying the following security-related issues and compliance risks:
- Infrequent encryption key rotation
- Lack of encryption
- Permission issue and errors
- Misconfiguration and compliance risks
- Missing multi-factor authentication
- Data storage exposed to public
- Misconfigurations
The above-listed loopholes help cloud owners reduce the chances of a successful cyber-attack and maintain consistency towards security issues.
CASB vs CSPM vs CWPP
All three cloud security challenges can help overcome cloud security complexity challenges in their own way, but how do they differ?
While CWPP protects workloads from the inside, Cloud Security Posture Management (CSPM) protects workloads from the outside by evaluating secure and compatible cloud platform control plane configurations.
Cloud Security Posture Management (CSPM) is a solution that integrates various use cases aimed at securing the cloud management plane, mainly by monitoring cloud resources and checking the cloud’s static configuration. Cloud Security Posture Management (CSPM) also evaluates the cloud platform management plan to determine if configurations are secure and compliant, using tools that support compliance monitoring, integration with DevOps processes, incident response, risk assessment, and risk visualization.
CASB, on the other hand, helps identify and block high-risk applications in real-time. The purpose of the CASB solution is to allow only authorized users to access the company’s crucial data. CASB can be deployed as API-based or proxy-based to detect threats in real-time.
CSPMs are also easy to set up and deploy as they use cloud service provider APIs to automate CIS audits, helping you avoid being another headline with an S3 bucket full of customer data exposed to the public or attackers.
CWPP focuses primarily on governance and security controls for cloud workloads. In contrast, compliance solutions focus on identifying the rules needed for specific compliance standards, warning about violations, and helping to fix deficiencies.
If your organization’s priority is protecting its cloud workloads and hardening application security, CWPP is likely the best choice. Similarly, if you need a security solution to monitor and report shadow IT issues faster, CASB can be the right option. And, if you want to perform continuous compliance monitoring and reduce misconfigurations, we recommend investing in Cloud Security Post Management (CSPM) solution.
Each cloud security solution has its own advantages and features making it a unique choice for your cloud environment security.
Conclusion
Chances of data theft, account hijacking, data breaches, and leakage have increased over the past few years. After the pandemic, we have seen a huge surge in cloud computing services. Many businesses are adopting cloud practices to improve their performance and save on cost.
But at the same time, businesses are exposing their data to new risks and challenges. With your data available in the public cloud, chances are high that you may face data privacy issues or data breaches.
Thus, to timely detect threats and protect your workloads, devices, and data in real-time, we have listed the three main cloud security solutions that can be highly advantageous for your cloud data security.
Cloud Access Security Broker (CASB) acts as a gateway to protect your data and applications from unauthorized users and monitors all managed and unmanaged SaaS and PaaS products.
On the other hand, the Cloud Workload Protection Platform (CWPP) is a highly distributed security tool used by enterprises to protect physical servers, containers, virtual machines (VMs), and serverless workloads.
Lastly, Cloud Security Posture Management (CSPM) is a group of security products and services used by enterprises to reduce misconfigurations and permission errors and prevent data storage from being exposed to the public.
Follow the above pointers to learn about each cloud security tool and how it can be advantageous for your business in different ways. Compare and invest in the one that suits your business requirement.